Cybersecurity as the Foundation for Management, Security, and Certification
IT and security officers, as well as management teams, face the challenge of assessing their information security holistically and making the right decisions. Increasing cyber threats, stricter regulatory requirements, and complex IT landscapes make it essential to regularly evaluate how well an organization is positioned – whether for benchmarking, optimizing existing measures, or preparing for certification. Yet, what is often missing is a structured, scalable approach that takes both individual requirements and legal obligations into account.
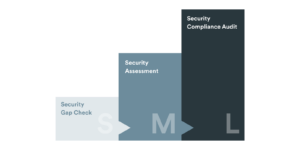
This is precisely where Consileon’s Cybersecurity Assessment comes in: modular in structure, practical in execution, and tailored to your specific needs. You gain a realistic picture of your security status along with precise recommendations for improvement. Depending on your scope, focus, and budget, the assessment ranges from a compact quick check to a certification-ready audit according to ISO/IEC 27001 or TISAX.
With the Consileon Cybersecurity Assessment, you receive a solid foundation for strategic management decisions, enabling targeted, appropriate investments that effectively reduce your business risks.